Healthc Inform Res.
2017 Jul;23(3):176-182. 10.4258/hir.2017.23.3.176.
Prevalence of Sharing Access Credentials in Electronic Medical Records
- Affiliations
-
- 1Department of Plastic Surgery, Hadassah-Hebrew University Medical Center, Jerusalem, Israel. ayalha@gmail.com
- 2Division of General Internal Medicine and Primary Care, Brigham and Women's Hospital, Harvard Medical School, Boston, MA, USA.
- 3Department of Dermatology, Hadassah-Hebrew University Medical Center, Jerusalem, Israel.
- 4Ben-Gurion University of the Negev, Be'er Sheva, Israel.
- 5Interdisciplinary Center, Herzliya, Israel.
- 6Duke University, Durham, NC, USA.
- KMID: 2403307
- DOI: http://doi.org/10.4258/hir.2017.23.3.176
Abstract
OBJECTIVES
Confidentiality of health information is an important aspect of the physician patient relationship. The use of digital medical records has made data much more accessible. To prevent data leakage, many countries have created regulations regarding medical data accessibility. These regulations require a unique user ID for each medical staff member, and this must be protected by a password, which should be kept undisclosed by all means.
METHODS
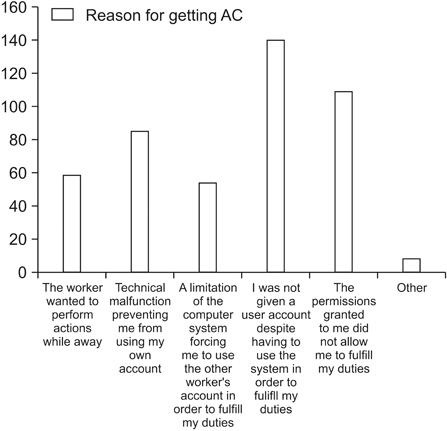
We performed a four-question Google Forms-based survey of medical staff. In the survey, each participant was asked if he/she ever obtained the password of another medical staff member. Then, we asked how many times such an episode occurred and the reason for it.
RESULTS
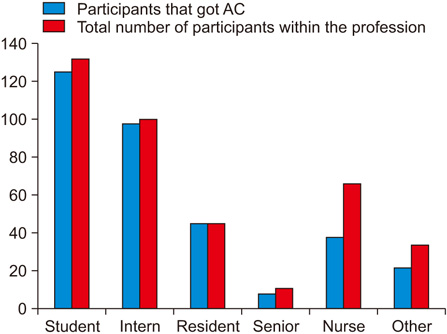
A total of 299 surveys were gathered. The responses showed that 220 (73.6%) participants reported that they had obtained the password of another medical staff member. Only 171 (57.2%) estimated how many time it happened, with an average estimation of 4.75 episodes. All the residents that took part in the study (45, 15%) had obtained the password of another medical staff member, while only 57.5% (38/66) of the nurses reported this.
CONCLUSIONS
The use of unique user IDs and passwords to defend the privacy of medical data is a common requirement in medical organizations. Unfortunately, the use of passwords is doomed because medical staff members share their passwords with one another. Strict regulations requiring each staff member to have it's a unique user ID might lead to password sharing and to a decrease in data safety.
Keyword
MeSH Terms
Figure
Reference
-
1. Aghadiuno M. Hippocrates appraises 21st century doctors. Br J Gen Pract. 2003; 53(497):984–985.2. Dorr Goold S, Lipkin M Jr. The doctor-patient relationship: challenges, opportunities, and strategies. J Gen Intern Med. 1999; 14:Suppl 1. S26–S33.3. Hesse BW, Hansen D, Finholt T, Munson S, Kellogg W, Thomas JC. Social participation in Health 2.0. Computer (Long Beach Calif). 2010; 43(11):45–52.
Article4. Benaloh J, Chase M, Horvitz E, Lauter K. Patient controlled encryption: ensuring privacy of electronic medical records. In : Proceedings of the 2009 ACM Workshop on Cloud Computing Security; 2009 Nov 13; Chicago, IL. p. 103–114.5. Fernandez-Aleman JL, Senor IC, Lozoya Pao, Toval A. Security and privacy in electronic health records: a systematic literature review. J Biomed Inform. 2013; 46(3):541–562.
Article6. Zurita L, Nohr C. Patient opinion: EHR assessment from the users perspective. Stud Health Technol Inform. 2004; 107(Pt 2):1333–1336.7. Chhanabhai P, Holt A. Consumers are ready to accept the transition to online and electronic records if they can be assured of the security measures. MedGenMed. 2007; 9(1):8.8. Strickland JH Jr, Hasson JH. A computer-controlled ventilator weaning system: a clinical trial. Chest. 1993; 103(4):1220–1226.9. US Department of Health & Human Services. The HIPAA Privacy Rule [Internet]. Washington (DC): US Department of Health & Human Services;c2016. cited at 2017 Jul 1. Available from: http://www.hhs.gov/ocr/privacy/hipaa/administrative/privacyrule/.10. Afek A. Protecting information in health related computer systems. Jerusalem: Israel Ministry of Health;2015.11. Response of the Ministry of Health CEO Circular - Protection of Information in Computerized Systems in the Health System - Circular 9/12 [Internet]. Jerusalem: Ministry of Health Israel;2012. cited at 2017 Jul 1. Available from:http://www.health.gov.il/hozer/mk18_2012.pdf.12. Breach Portal: Notice to the Secretary of HHS Breach of Unsecured Protected Health Information. Washington (DC): US Department of Health and Human Services Office for Civil Rights;c2016. cited at 2017 Jul 1. Available from: https://ocrportal.hhs.gov/ocr/breach/wizard_breach.jsf?faces-redirect=true.13. Lost flash drive at core of Kaiser Permanente Data Breach [Internet]. place unknown: CRN.com;c2013. cited at 2017 Jul 1. http://www.crn.com/news/security/240164674/lost-flash-drive-at-core-of-kaiser-permanente-data-breach.htm.14. Watson ST, Miller M. Mass email by Dent Neurologic inadvertently breaches privacy of 10,200 patients [Internet]. Buffalo (NY): The Buffalo News;c2013. cited at 2017 Jul 1. Available from: http://buffalonews.com/2013/05/14/mass-email-by-dent-neurologic-inadvertently-breaches-privacy-of-10200-patients/.15. Salman J. Patient data may have been leaked, doctors group warns [Internet]. Sarasota (FL): Herald-Tribune;c2013. cited at 2017 Jul 1. http://www.heraldtribune.com/news/20131125/patient-data-may-have-been-leaked-doctors-group-warns.16. Hassidim A. Health information security survey. place unknown: publisher unknown;2014.17. Reason J. Human error: models and management. BMJ. 2000; 320(7237):768–770.
Article18. Flink CW. Weakest link in information system security. In : Proceedings of the Workshop for Application of Engineering Principles to System Security Design (WAEPSSD); 2002 Nov 6-8; Boston, MA.19. Haas S, Wohlgemuth S, Echizen I, Sonehara N, Muller G. Aspects of privacy for electronic health records. Int J Med Inform. 2011; 80(2):e26–e31.
Article20. Gino F, Ayal S. Contagion and differentiation in unethical behavior the effect of one bad apple on the barrel. Psychol Sci. 2009; 20(3):393–398.
Article21. Welsh DT, Ordóñez LD, Snyder DG, Christian MS. The slippery slope: how small ethical transgressions pave the way for larger future transgressions. J Appl Psychol. 2015; 100(1):114–127.
Article22. Buhrmester M, Kwang T, Gosling SD. Amazon,s Mechanical Turk: a new source of inexpensive, yet high-quality, data? Perspect Psychol Sci. 2011; 6(1):3–5.
Article
- Full Text Links
- Actions
-
Cited
- CITED
-
- Close
- Share
- Similar articles
-
- Patient Consent Management by a Purpose-Based Consent Model for Electronic Health Record Based on Blockchain Technology
- Nurses’ Experiences with the Use of Electronic Nursing Record: A Qualitative Study
- Cost-Benefit Analysis of the Sharing System for Electronic Patients Records Among Healthcare Institutions
- Secondary Use Provisions in the European Health Data Space Proposal and Policy Recommendations for Korea
- Comparison of Nursing Records of Open Heart Surgery Patients before and after Implementation of Electronic Nursing Record