Healthc Inform Res.
2012 Jun;18(2):125-135. 10.4258/hir.2012.18.2.125.
Pitfalls and Security Measures for the Mobile EMR System in Medical Facilities
- Affiliations
-
- 1Center for Medical Informatics, Seoul National University Bundang Hospital, Seongnam, Korea. yoosoo0@snu.ac.kr
- 2Department of Family Medicine, Seoul National University Bundang Hospital, Seongnam, Korea.
- 3Department of Neurology, Seoul National University Bundang Hospital, Seongnam, Korea.
- 4Department of Thoracic and Cardiovascular Surgery, Seoul National University Bundang Hospital, Seongnam, Korea.
- 5Department of Conservative Dentistry, Seoul National University Bundang Hospital, Seongnam, Korea.
- 6Department of Otorhinolaryngology, Seoul National University Bundang Hospital, Seongnam, Korea.
- 7Department of Plastic and Reconstructive Surgery, Seoul National University Bundang Hospital, Seongnam, Korea.
- KMID: 2045576
- DOI: http://doi.org/10.4258/hir.2012.18.2.125
Abstract
OBJECTIVES
The goal of this paper is to examine the security measures that should be reviewed by medical facilities that are trying to implement mobile Electronic Medical Record (EMR) systems designed for hospitals.
METHODS
The study of the security requirements for a mobile EMR system is divided into legal considerations and sectional security investigations. Legal considerations were examined with regard to remote medical services, patients' personal information and EMR, medical devices, the establishment of mobile systems, and mobile applications. For the 4 sectional security investigations, the mobile security level SL-3 from the Smartphone Security Standards of the National Intelligence Service (NIS) was used.
RESULTS
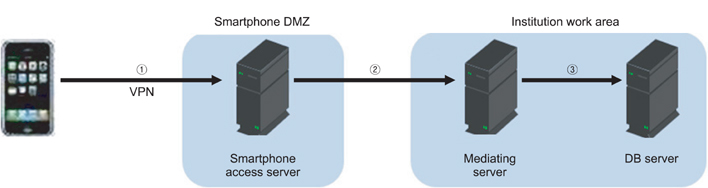
From a compliance perspective, legal considerations for various laws and guidelines of mobile EMR were executed according to the model of the legal considerations. To correspond to the SL-3, separation of DMZ and wireless network is needed. Mobile access servers must be located in only the smartphone DMZ. Furthermore, security measures like 24-hour security control, WIPS, VPN, MDM, and ISMS for each section are needed to establish a secure mobile EMR system.
CONCLUSIONS
This paper suggested a direction for applying regulatory measures to strengthen the security of a mobile EMR system in accordance with the standard security requirements presented by the Smartphone Security Guideline of the NIS. A future study on the materialization of these suggestions after their application at actual medical facilities can be used as an illustrative case to determine the degree to which theory and reality correspond with one another.
Keyword
Figure
Cited by 3 articles
-
Implementation Issues of Virtual Desktop Infrastructure and Its Case Study for a Physician's Round at Seoul National University Bundang Hospital
Sooyoung Yoo, Seok Kim, Taegi Kim, Jon Soo Kim, Rong-Min Baek, Chang Suk Suh, Chin Youb Chung, Hee Hwang
Healthc Inform Res. 2012;18(4):259-565. doi: 10.4258/hir.2012.18.4.259.Development of Mobile Platform Integrated with Existing Electronic Medical Records
YoungAh Kim, Sung Soo Kim, Simon Kang, Kyungduk Kim, Jun Kim
Healthc Inform Res. 2014;20(3):231-235. doi: 10.4258/hir.2014.20.3.231.Technology Acceptance and Adoption of Innovative Smartphone Uses among Hospital Employees
Byung Chan Moon, Hyejung Chang
Healthc Inform Res. 2014;20(4):304-312. doi: 10.4258/hir.2014.20.4.304.
Reference
-
1. Korea Communications Commission. Ministry of Public Administration and Security. Ministry of Knowledge Economy. National information security white paper. 2011. Seoul, Korea: Korea Communications Commission;278–279.2. 148Apps.biz. App store metrics [Internet]. c2012. cited at 2012 Feb 1. TrouserMac Industries;Available from: http://148apps.biz/app-store-metrics/?mpage=catcount.3. Ministry of Public Administration and Security. 2011 National informatization white paper. 2011. Seoul, Korea: Ministry of Public Administration and Security;323–326.4. Min JH. The study of security measures of threat on mobile internet environment [dissertation]. 2010. Seoul, Korea: Konkuk University.5. Jang SJ. IT planning series: the trend of mobile computing security technology. 2011. Seoul, Korea: National IT Industry Promotion Agency;12–20.6. Ho AJ. Security of smartphone pouring. Inf Secur 21C. 2010. 114:54.7. Park HW. Start to prepare the security, safe receipt of mobile office. Inf Secur 21C. 2010. 124:75.8. National Intelligence Service. Security standards for smartphones for business use by national and public institutions. 2010. Seoul, Korea: National Intelligence Service.9. Poon EG, Keohane CA, Yoon CS, Ditmore M, Bane A, Levtzion-Korach O, Moniz T, Rothschild JM, Kachalia AB, Hayes J, Churchill WW, Lipsitz S, Whittemore AD, Bates DW, Gandhi TK. Effect of bar-code technology on the safety of medication administration. N Engl J Med. 2010. 362:1698–1707.
Article10. Paoletti RD, Suess TM, Lesko MG, Feroli AA, Kennel JA, Mahler JM, Sauders T. Using bar-code technology and medication observation methodology for safer medication administration. Am J Health Syst Pharm. 2007. 64:536–543.
Article11. Ministry of Health and Welfare. Medical facility personal information protection guideline. 2010. Seoul, Korea: Ministry of Health and Welfare.12. Ministry of Public Administration and Security. Notification of privacy impact assessment (2011-39). 2011. Seoul, Korea: Ministry of Public Administration and Security.13. Korea Food and Drug Administration. Mobile PACS licensing examination guideline. 2011. Seoul, Korea: Korea Food and Drug Administration.14. Choi MG. Report No.: NCSC-TR050021. Security measures for safe use of wireless-LAN. 2005. Seoul, Korea: National Cyber Security Center.15. Hacking Response Team, Korea Internet and Security Agency. Wireless LAN security guide. 2010. Seoul, Korea: Korea Internet and Security Agency.16. Center for Cyber Response, Financial Security Agency. Report No.: FSA 2010-08. Smartphone security guide in the banking sector. 2010. Seoul, Korea: Financial Security Agency.17. Ministry of Public Administration and Security. Reg. No.: 11-1311000-000330-10. Information system SW development security guide. 2011. Seoul, Korea: Ministry of Public Administration and Security.18. Ministry of Public Administration and Security. Information system establishment and operation guideline (2012-12). 2012. Seoul, Korea: Ministry of Public Administration and Security.19. Public SW Security Team, Korea Internet and Security Agency. Mobile application security certification guide v1.0. 2011. Seoul, Korea: Korea Internet and Security Agency.20. Ministry of Public Administration and Security. Standards for measures to warrant security of personal information (2011-43). 2011. Seoul, Korea: Ministry of Public Administration and Security.21. Korea Communications Commission. Korea Internet and Security Agency. Guide to using smartphone vaccine. 2011. Seoul, Korea: Korea Communications Commission.22. Park JH. The latest IT trend: the core of multiplatform mobile strategy, MDM solution. 2012. Seoul, Korea: National IT Industry Promotion Agency.23. Min SS. Report No.: TM-01. Security threat of mobile office and MDM solution. 2011. Seoul, Korea: Financial Security Agency.24. Kim YT. Report No.: vol. 2011-017. Issue report: information security and Introduction of personal information management framework. 2011. Seoul, Korea: Financial Security Agency.25. Ministry of Public Administration and Security. The e-government ISMS certification guideline (2010-178). 2010. Seoul, Korea: Ministry of Public Administration and Security.
- Full Text Links
- Actions
-
Cited
- CITED
-
- Close
- Share
- Similar articles
-
- Development of Mobile Platform Integrated with Existing Electronic Medical Records
- Measures to address obstetrically underserved areas: limitations and future directions
- Factors affecting the users'satisfaction on the electronic medical record system
- Detrimental impact of cell phone radiation on sperm DNA integrity
- Personal Privacy Protection of Electronic Medical Record in Health Information System