Healthc Inform Res.
2015 Oct;21(4):271-282. 10.4258/hir.2015.21.4.271.
Service-Oriented Security Framework for Remote Medical Services in the Internet of Things Environment
- Affiliations
-
- 1Department of Information Technology Team, National Cancer Center, Goyang, Korea. kkido@ncc.re.kr
- KMID: 2166877
- DOI: http://doi.org/10.4258/hir.2015.21.4.271
Abstract
OBJECTIVES
Remote medical services have been expanding globally, and this is expansion is steadily increasing. It has had many positive effects, including medical access convenience, timeliness of service, and cost reduction. The speed of research and development in remote medical technology has been gradually accelerating. Therefore, it is expected to expand to enable various high-tech information and communications technology (ICT)-based remote medical services. However, the current state lacks an appropriate security framework that can resolve security issues centered on the Internet of things (IoT) environment that will be utilized significantly in telemedicine.
METHODS
This study developed a medical service-oriented frame work for secure remote medical services, possessing flexibility regarding new service and security elements through its service-oriented structure. First, the common architecture of remote medical services is defined. Next medical-oriented secu rity threats and requirements within the IoT environment are identified. Finally, we propose a "service-oriented security frame work for remote medical services" based on previous work and requirements for secure remote medical services in the IoT.
RESULTS
The proposed framework is a secure framework based on service-oriented cases in the medical environment. A com parative analysis focusing on the security elements (confidentiality, integrity, availability, privacy) was conducted, and the analysis results demonstrate the security of the proposed framework for remote medical services with IoT.
CONCLUSIONS
The proposed framework is service-oriented structure. It can support dynamic security elements in accordance with demands related to new remote medical services which will be diversely generated in the IoT environment. We anticipate that it will enable secure services to be provided that can guarantee confidentiality, integrity, and availability for all, including patients, non-patients, and medical staff.
Keyword
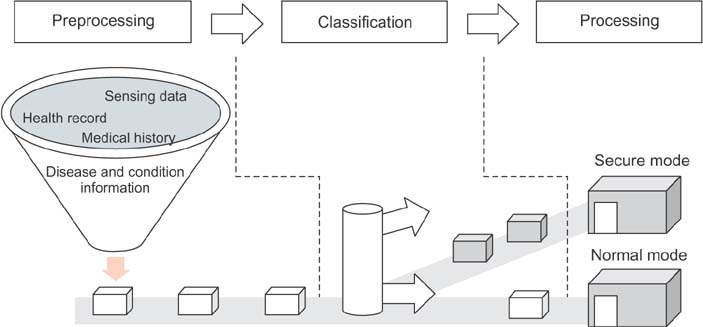
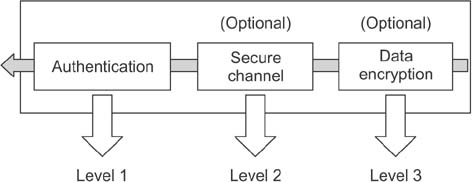
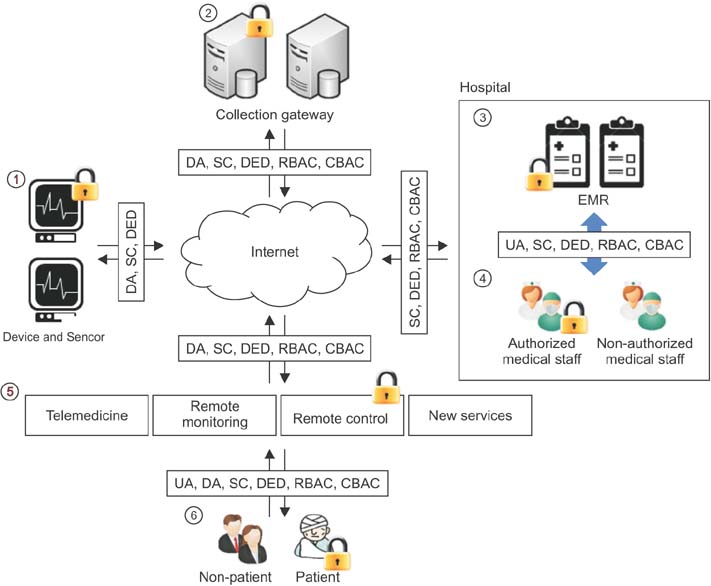
Figure
Cited by 1 articles
-
Privacy Enhanced Healthcare Information Sharing System for Home-Based Care Environments
Daniel Agbesi Dzissah, Joong-Sun Lee, Hiroyuki Suzuki, Mie Nakamura, Takashi Obi
Healthc Inform Res. 2019;25(2):106-114. doi: 10.4258/hir.2019.25.2.106.
Reference
-
1. Liang X, Li X, Barua M, Chen L, Lu R, Shen X, et al. Enable pervasive healthcare through continuous remote health monitoring. IEEE Wirel Commun. 2012; 19(6):10–18.2. Li KF. Smart home technology for telemedicine and emergency management. J Ambient Intell Humaniz Comput. 2013; 4(5):535–546.
Article3. Xu B, Xu L, Cai H, Xie C, Hu J, Bu F. Ubiquitous data accessing method in IoT-based information system for emergency medical services. IEEE Trans Industr Inform. 2014; 10(2):1578–1586.
Article4. Chiuchisan I, Costin HN, Geman O. Adopting the internet of things technologies in health care systems. In : Proceedings of 2014 International Conference and Exposition on Electrical and Power Engineering (EPE); 2014 Oct 16-18; Iasi, Romania. p. 532–535.5. Wootton R. Twenty years of telemedicine in chronic disease management: an evidence synthesis. J Telemed Telecare. 2012; 18(4):211–220.
Article6. Ryu S. Telemedicine: opportunities and developments in member states: report on the Second Global Survey on eHealth 2009. Healthc Inform Res. 2012; 18(2):153–155.
Article7. Nguyen KT, Laurent M, Oualha N. Survey on secure communication protocols for the Internet of Things. Ad Hoc Netw. 2015; 32:17–31.
Article8. Sicari S, Rizzardi A, Grieco LA, Coen-Porisini A. Security, privacy and trust in Internet of Things: the road ahead. Comput Netw. 2015; 76:146–164.
Article9. Vucinic M, Tourancheau B, Rousseau F, Duda A, Damon L, Guizzetti R. OSCAR: object security architecture for the Internet of Things. Ad Hoc Netw. 2014; 32:3–16.
Article10. Doukas C, Maglogiannis I, Koufi V, Malamateniou F, Vassilacopoulos G. Enabling data protection through PKI encryption in IoT m-Health devices. In : Proceedings of 2012 IEEE 12th International Conference on Bioinformatics & Bioengineering (BIBE); 2012 Nov 11-13; Larbaca, Cyprus. p. 25–29.11. Hsu WS, Pan JI. Secure mobile agent for telemedicine based on P2P networks. J Med Syst. 2013; 37(3):9947.
Article12. Al Ameen M, Liu J, Kwak K. Security and privacy issues in wireless sensor networks for healthcare applications. J Med Syst. 2012; 36(1):93–101.
Article13. Camara C, Peris-Lopez P, Tapiador JE. Security and privacy issues in implantable medical devices: a comprehensive survey. J Biomed Inform. 2015; 55:272–289.
Article14. Zaidan BB, Haiqi A, Zaidan AA, Abdulnabi M, Kiah ML, Muzamel H. A security framework for nationwide health information exchange based on telehealth strategy. J Med Syst. 2015; 39(5):51.
Article15. Li M, Yu S, Zheng Y, Ren K, Lou W. Scalable and secure sharing of personal health records in cloud computing using attribute-based encryption. IEEE Trans Parallel Distrib Syst. 2013; 24(1):131–143.
Article16. Savola RM, Abie H, Sihvonen M. Towards metricsdriven adaptive security management in e-health IoT applications. In : Proceedings of the 7th International Conference on Body Area Networks; 2012 Sep 24-26; Oslo, Norway. p. 276–281.17. Moosavi SR, Gia TN, Rahmani AM, Nigussie E, Virtanen S, Isoaho J, et al. SEA: a secure and efficient authentication and authorization architecture for IoT-based healthcare using smart gateways. Procedia Comput Sci. 2015; 52:452–459.
Article18. Simplicio MA Jr, Iwaya LH, Barros BM, Carvalho TC, Naslund M. SecourHealth: a delay-tolerant security framework for mobile health data collection. IEEE J Biomed Health Inform. 2015; 19(2):761–772.
Article19. Saleem S, Ullah S, Kwak KS. A study of IEEE 802.15.4 security framework for wireless body area networks. Sensors (Basel). 2011; 11(2):1383–1395.
Article20. Zhang XM, Zhang N. An open, secure and flexible platform based on internet of things and cloud computing for ambient aiding living and telemedicine. In : Proceedings of 2011 International Conference on Computer and Management (CAMAN); 2011 May 19-21; Wuhan, China. p. 1–4.21. Shini SG, Thomas T, Chithraranjan K. Cloud based medical image exchange-security challenges. Procedia Eng. 2012; 38:3454–3461.
Article22. Chen HM, Lo JW, Yeh CK. An efficient and secure dynamic ID-based authentication scheme for telecare medical information systems. J Med Syst. 2012; 36(6):3907–3915.
Article23. Jiang Q, Ma J, Ma Z, Li G. A privacy enhanced authentication scheme for telecare medical information systems. J Med Syst. 2013; 37(1):9897.
Article24. Das AK, Goswami A. A secure and efficient uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. J Med Syst. 2013; 37(3):9948.
Article25. Kim KW, Lee JD. On the security of two remote user authentication schemes for telecare medical information systems. J Med Syst. 2014; 38(5):17.
Article26. Das AK, Goswami A. An enhanced biometric authentication scheme for telecare medicine information systems with nonce using chaotic hash function. J Med Syst. 2014; 38(6):27.
Article27. Shin M. Secure remote health monitoring with unreliable mobile devices. J Biomed Biotechnol. 2012; 2012:546021.
Article28. Abie H, Balasingham I. Risk-based adaptive security for smart IoT in eHealth. In : Proceedings of the 7th International Conference on Body Area Networks; 2012 Sep 24-26; Oslo, Norway. p. 269–275.29. Al-Haj A, Amer A. Secured telemedicine using region-based watermarking with tamper localization. J Digit Imaging. 2014; 27(6):737–750.
Article
- Full Text Links
- Actions
-
Cited
- CITED
-
- Close
- Share
- Similar articles
-
- Internet of Things: An Overview and its Applications in Aviation
- Action Research on Development and Application of Internet of Things Services in Hospital
- Medical Consultation and Telemedicine Using the Internet
- Exploratory Study on Customer-Oriented Service Contact Elements in Foodservice Industry
- Determinant factors on the adoption of application service providers in hospital information systems