Healthc Inform Res.
2010 Mar;16(1):22-29. 10.4258/hir.2010.16.1.22.
A Selective Encryption Algorithm Based on AES for Medical Information
- Affiliations
-
- 1Department of Information & Media, Kyungin Woman's College, Incheon, Korea.
- 2Department of Computer Science, Kangwon National University, Chuncheon, Korea. saneya@kangwon.ac.kr
- 3Department of Medical Instrument and Information, Hallym College, Chuncheon, Korea.
- KMID: 2166562
- DOI: http://doi.org/10.4258/hir.2010.16.1.22
Abstract
OBJECTIVES
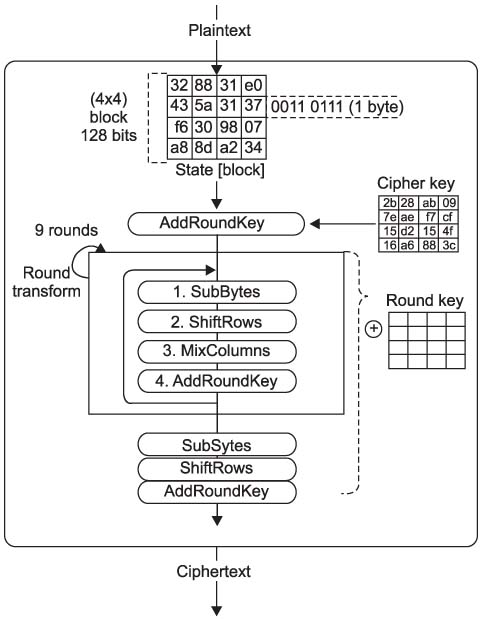
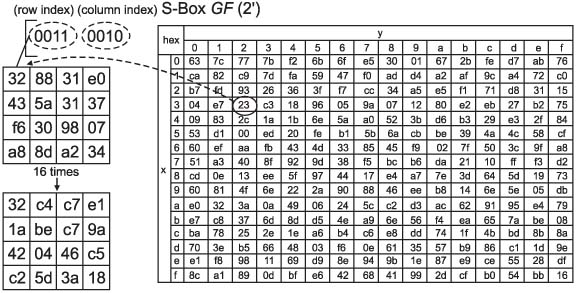
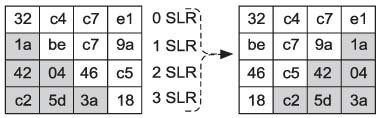
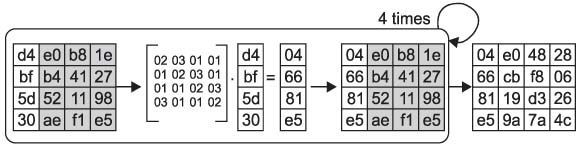
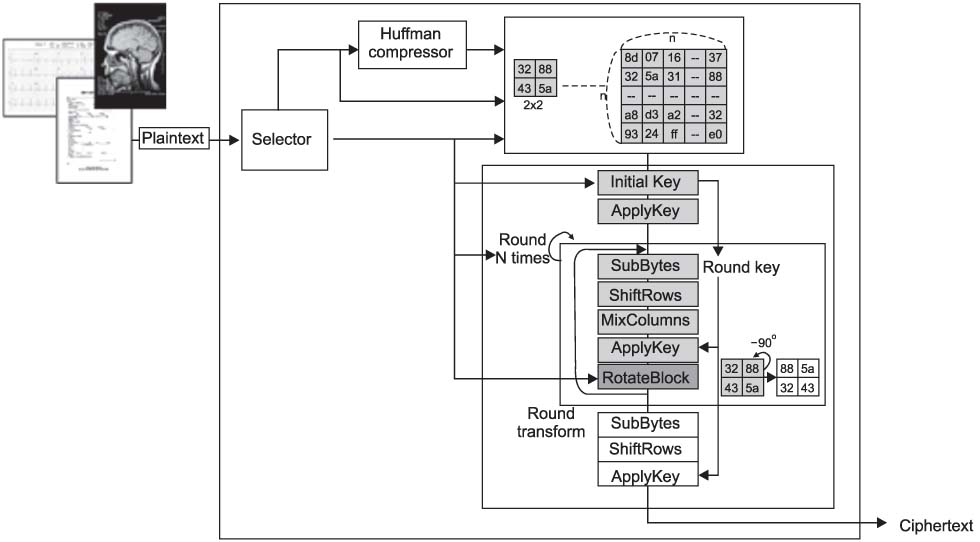
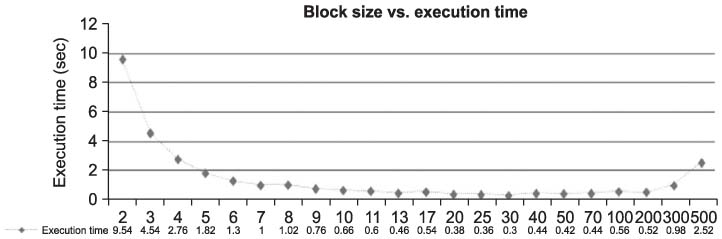
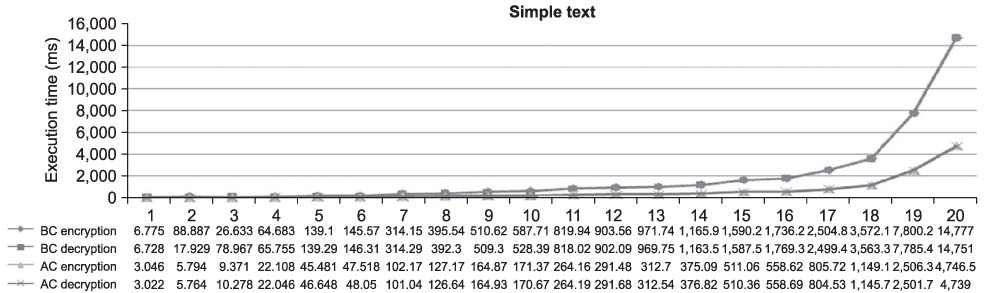
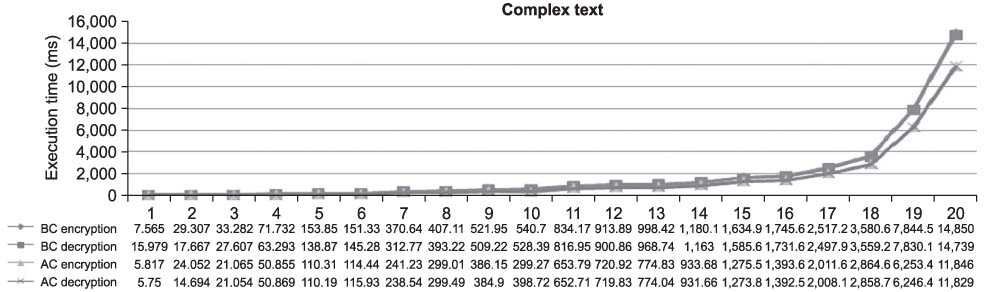
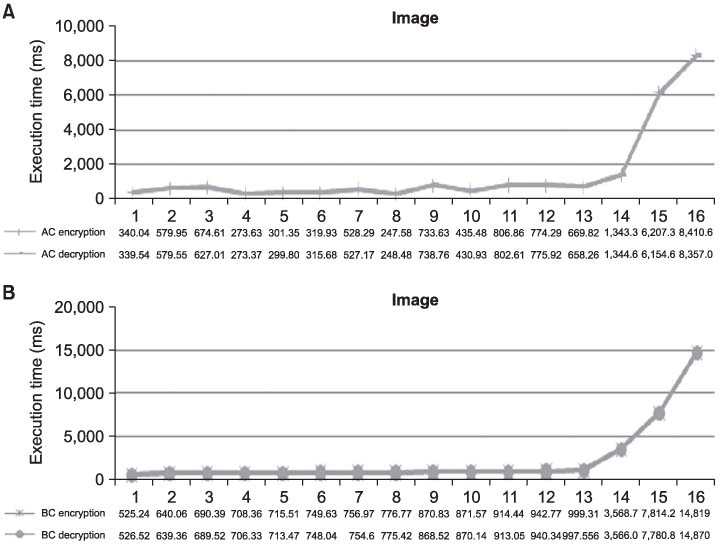
The transmission of medical information is currently a daily routine. Medical information needs efficient, robust and secure encryption modes, but cryptography is primarily a computationally intensive process. Towards this direction, we design a selective encryption scheme for critical data transmission. METHODS: We expand the advandced encrytion stanard (AES)-Rijndael with five criteria: the first is the compression of plain data, the second is the variable size of the block, the third is the selectable round, the fourth is the optimization of software implementation and the fifth is the selective function of the whole routine. We have tested our selective encryption scheme by C++ and it was compiled with Code::Blocks using a MinGW GCC compiler. RESULTS: The experimental results showed that our selective encryption scheme achieves a faster execution speed of encryption/decryption. In future work, we intend to use resource optimization to enhance the round operations, such as SubByte/InvSubByte, by exploiting similarities between encryption and decryption. CONCLUSIONS: As encryption schemes become more widely used, the concept of hardware and software co-design is also a growing new area of interest.
Keyword
MeSH Terms
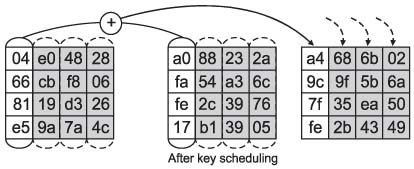
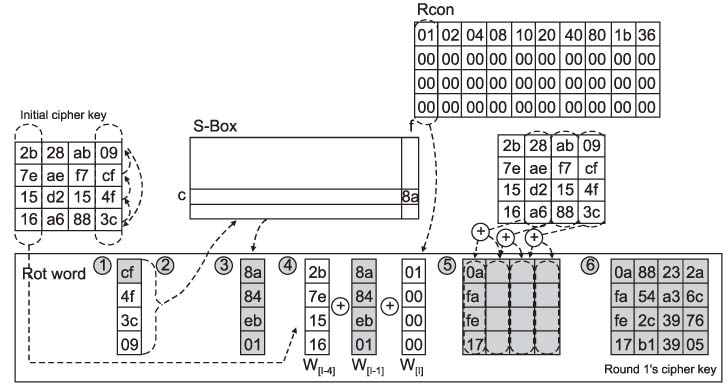
Figure
Reference
-
1. Choe J, Kim NH, Yoo SK. Web-based secure access from multiple patient reservoirs. J Korean Soc Med Inform. 2004. 10:269–278.
Article2. Choi S. Development of a cyber medical training system by using internet MPEG technology. J Korean Soc Med Inform. 2004. 10:167–174.
Article3. Yoo YS, Lee HJ, Park JY, Jung SH. The effect of introduction of picture archiving and communication system on interpretation rate of radiologic examinations. J Korean Soc Med Inform. 2007. 13:349–359.
Article4. Yang DI, Park SH, Chon KH. Design and implementation of pulse-diagnosis ontology in ubiquitous computing environment. J Korean Soc Med Inform. 2008. 14:45–54.
Article5. Paul AJ, Paul V, Mythili P. A fast and secure encryption algorithm for message communication. Proceedings of IET-UK International Conference on Information and Communication Technology in Electrical Sciences. 2007. 2007 Dec 20-22; TamilNadu, IN. Hertfordshire (UK): Institution of Engineering and Technology;629–634.
Article6. Islam N, Mia HM, Chowdhury IF, Martin MA. Lee R, Muenchaisri P, Dosch W, editors. Effect of security increment to symmetric data encryption through AES methodology. Proceedings of 9th ACIS International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing. 2008. 2008 Aug 6-8; Phuket, TH. Los Alamitos (CA): IEEE Computer Society;291–294.
Article7. Lopez-Ongil C, Jimenez-Horas A, Portela-Garcia M, Garcia-Valderas M, San Millan E, Entrena L. Gizopoulos D, Seifert N, Nicolaidis M, Paschalis A, editors. Smart hardening for round-based encryption algorithms: application to advanced encryption standard. Proceedings of the 2008 14th IEEE International OnLine Testing Symposium. 2008. 2008 Jul 7-9; Rhodes, GR. Los Alamitos (CA): IEEE Computer Society;167–168.8. Xiao Y, Sun B, Chen HH, Cuizani S, Wang R. Performance analysis of advanced encryption standard (AES). Proceedings of IEEE GLOBECOM 2006. 2006. 2006 Nov 27-Dec 1; San Francisco, CA. Washington (DC): IEEE Communications Society;1–5.9. Bahrak B, Aref MR. Impossible differential attack on seven-round AES-128. IET Inf Secur. 2008. 2:28–32.
Article10. Doomun R, Doma J, Tengur S. Zaman HB, Sembok TM, van Rijsbergen K, Zadeh L, Bruza P, Shih T, editors. AES-CBC software execution optimization. Proceedings of International Symposium on Information Technology 2008. 2008. 2008 Aug 26-29; Kuala Lumpur, MY. Institute of Electrical and Electronics Engineers Inc.;1–8.
Article11. Gogniat G, Wolf T, Burleson W, Diguet JP, Bossuet L, Vaslin R. Reconfigurable hardware for high-Security/high-Performance embedded systems: the SAFES perspective. IEEE Trans Very Large Scale Integr (VLSI) Syst. 2008. 16:144–155.
Article
- Full Text Links
- Actions
-
Cited
- CITED
-
- Close
- Share
- Similar articles
-
- Web-based Secure Access from Multiple Patient Reservoirs
- Implementation of a Particle Swarm Optimization-based Classification Algorithm for Analyzing DNA Chip Data
- Segmentation of Hippocampus in Human Brain MRI Using Watersnakes
- An Improved Mesh Simplification Algorithm Based on Quadric Error Metrics
- A Priority Anti-collision Algorithm Based on RFID in Healthcare Environment